App Control REST API Authentication
Carbon Black App Control is the new name for the product formerly called CB Protection.
Each Carbon Black App Control user has a personal API key. That API key confers all rights and capabilities assigned to that user to anyone possessing the API key. Therefore, treat your API key as you would your password. If the API Token is missing or compromised, you can reset the API key to generate a new token and revoke any previous API keys issued to a user. It is recommended that you create separate user contexts for each API use case, with the minimum set of privileges required for each API script to function. See the Carbon Black App Control User Guide for more information on how to set up User Groups and Role Based Access Control in the console.
To find a API key corresponding with a particular Carbon Black App Control user account, log into the console as an administrator, then select Administration -> Login Accounts. Find the user in the list then click the “Edit” button on the left hand side of the row containing their username.
This will show the details for the selected user. At the bottom of the details page, click the checkbox next to “Show API Token” in the API section. This will reveal the API token associated with the given user. If no API token is revealed, click the “Generate” button. If a new API token was created, it must be saved with the “Save” button before it becomes active.
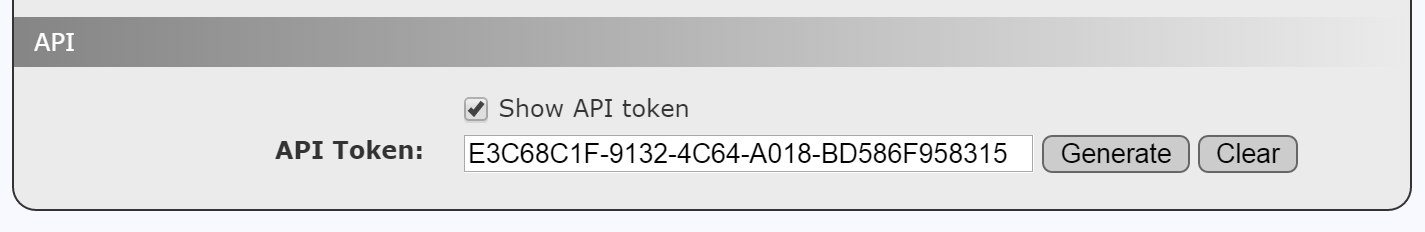
Add this key to a custom HTTP Request Header X-Auth-Token.
For example, to get the list of public events published by the server:
$ curl -k -H 'X-Auth-Token: E3C68C1F-9132-4C64-A018-BD586F958315' https://192.168.215.128/api/bit9platform/v1/event
[
{
"id": 1,
"computerId": null,
"fileCatalogId": null,
"installerFileCatalogId": null,
"processFileCatalogId": null,
"fileName": null,
"pathName": null,
"timestamp": "2016-01-11T18:34:45.84Z",
"receivedTimestamp": "2016-01-11T18:34:45.84Z",
"description": "Notifier 'Enforce tamper protection' was created by 'System'",
"severity": 6,
"type": 3,
"subtype": 153,
"subtypeName": "Notifier created",
"ipAddress": null,
"userName": "System",
"ruleName": null,
"banName": null,
"updaterName": null,
"indicatorName": null,
"commandLine": "",
"processKey": "",
"computerName": null,
"processPathName": null,
"processFileName": null,
"installerFileName": "",
"param1": "Enforce tamper protection",
"param2": null,
"param3": null,
"policyId": null,
"policyName": "",
"stringId": 294
},
...
]Last modified on December 28, 2015